Announcing DoltLab Enterprise Edition
We launched DoltLab, the self-hosted version of DoltHub.com back in January 2022 as a way to support users who wanted to harness the power of Dolt, but not push their data to the public internet.
From that point on, we've consistently improved DoltLab and added powerful features to best support our customers' use cases and deployment requirements. Since then, DoltLab has become one of our most popular and sought after products.
Today we're excited to announce the release of DoltLab v2.0.0, which includes built-in support for DoltLab Enterprise!
Designed for DoltLab Enterprise customers, a DoltLab Enterprise instance includes a number of exclusive features that are not available in DoltLab Core, the free version of DoltLab. These customers also receive full engineering support, prioritization of new DoltLab features and issues, and also play a major part in driving DoltLab's roadmap.
In this blog, I'll cover how to configure your DoltLab v2.0.0 instance to run in enterprise mode and enable its exclusive feature set.
Be advised, if you are currently a non-enterprise user of DoltLab <= v1.1.1 and are using the following features, upgrading to DoltLab v2.0.0 will disable them on your instance.
- Custom Automated Emails
- Custom Logo
- Custom Color Themes
- Super Admins
If you're interested in finding out how you or your team can become DoltLab Enterprise customers, please reach out to Brian Fitzgerald at brianf@dolthub.com or @brianfitz on our Discord server.
DoltLab Enterprise Up and Running
After upgrading to DoltLab v2.0.0, you'll only need to supply the following additional environment variables to the ./start-doltlab.sh script to run your instance in enterprise mode:
...
DOLTLAB_ENTERPRISE_ONLINE_PRODUCT_CODE=<Product Code> \
DOLTLAB_ENTERPRISE_ONLINE_SHARED_KEY=<Shared Key> \
DOLTLAB_ENTERPRISE_ONLINE_API_KEY=<API Key> \
DOLTLAB_ENTERPRISE_ONLINE_LICENSE_KEY=<License Key> \
DOLTLAB_ENTERPRISE_HARDWARE_ID=<Hardware ID>
./start-doltlab.shUpon becoming an enterprise client, we will supply you the values to use for DOLTLAB_ENTERPRISE_ONLINE_PRODUCT_CODE, DOLTLAB_ENTERPRISE_ONLINE_SHARED_KEY, DOLTLAB_ENTERPRISE_ONLINE_API_KEY, and DOLTLAB_ENTERPRISE_ONLINE_LICENSE_KEY. You can run ./get_machine_id, a binary included with DoltLab v2.0.0, to get the value for DOLTLAB_ENTERPRISE_HARDWARE_ID.
To run enterprise mode successfully, all of these variables are required and must contain valid values.
Please note, at this time, DoltLab Enterprise requires egress access to the public internet in order to successfully validate enterprise licenses. Support for offline and air-gapped instances will be added in the future.
Your DoltLab instance is now running in enterprise mode, granting you access to enterprise exclusive features!
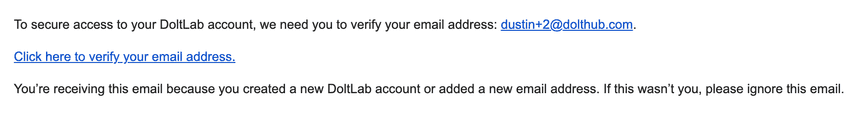
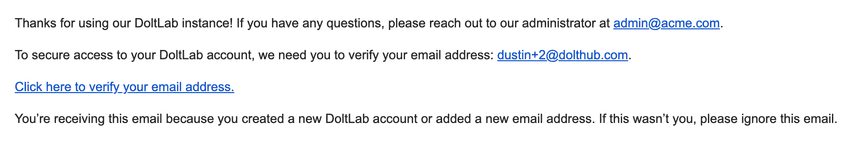
Custom Automated Emails
Included with DoltLab are template files DoltLab uses to generate the emails it sends to users. These can be customized in enterprise mode to contain bespoke content for users of your instance.
Follow the steps laid out in the DoltLab documentation for more detailed information about customizing these templates.
You will need to restart your DoltLab instance for the changes to take effect.
Before.
After.
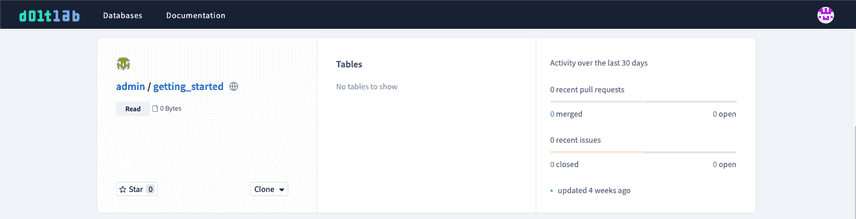
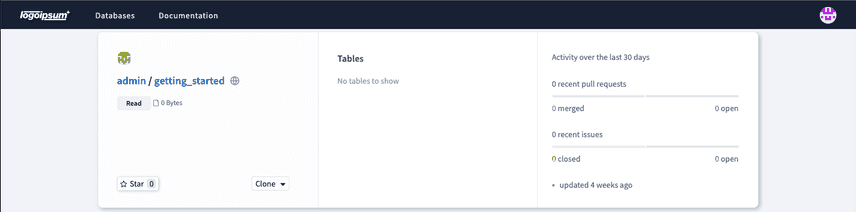
Custom Logo
To use a custom logo on your DoltLab instance, create a file called ./admin-config.yaml that contains the following:
enterprise:
logo: "/path/to/custom-logo.png"This logo field should contain an absolute path to the custom logo file on your DoltLab host.
After saving ./admin-config.yaml, restart DoltLab and you will see your instance with an updated logo.
Before.
After.
Super Admins
A Super Admin is a DoltLab user granted unrestricted access and the highest possible permission level on all organizations, teams, and databases on a DoltLab instance.
These users can write to any database, public or private, merge pull-requests, delete databases and add or remove organization/team members.
By default there are no "super admins" registered on a DoltLab instance (including the default user admin) but these super admin users can be added by defining a super_admins field in ./admin-config.yaml.
enterprise:
logo: "/path/to/custom-logo.png"
super_admins: ["email@example.com"]In the super_admins field, specify a list of email addresses for the user(s) who should have super admin permissions.
DoltLab must be restarted for this configuration to take effect.
Custom Color Themes
The color scheme of a DoltLab instance can be customized by editing the ./admin-config.yaml and adding a theme.custom block.
enterprise:
logo: "/path/to/custom-logo.png"
super_admins: ["email@example.com"]
theme:
custom:
rgb_accent_1: "255, 210, 4"
rgb_background_accent_1: "48, 48, 48"
rgb_background_gradient_start: "68, 69, 69"
rgb_button_1: "12, 192, 112"
rgb_button_2: "48, 48, 48"
rgb_link_1: "12, 192, 112"
rgb_link_2: "48, 48, 48"
rgb_link_light: "144, 238, 144"Here you are free to specify RGB color values in any of the rgb_* fields which will override the default DoltLab color values. The RGB values used in the configuration example above appear as:
Single-Sign-On
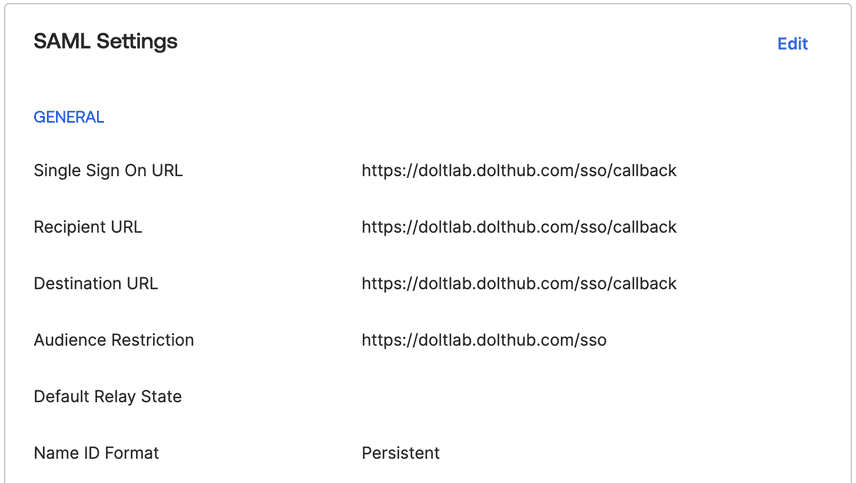
Additionally, DoltLab Enterprise also supports SAML single-sign-on! To configure your DoltLab instance to use single-sign-on, you will first need an Identity Provider (IP) to provide you with a metadata descriptor.
For example, Okta, a popular IP, provides an endpoint for downloading the metadata descriptor for a SAML application after you register an application on their platform.
During registration, Okta will ask you for the "Single Sign On Url" and an "Audience Restriction" for the application.
Use the domain/host IP address of your DoltLab instance followed by /sso/callback for the "Single Sign On Url", and use that same domain/host IP address followed by just "/sso" for the "Audience Restriction". Since this example will be for https://doltlab.dolthub.com, we'll use https://doltlab.dolthub.com/sso/callback and https://doltlab.dolthub.com/sso respectively.
Be sure to also set "Name ID Format" to "Persistent".
Then, download the metadata Okta provides for this application to your DoltLab host.
Next, run the ./gen_saml_certs.sh script included with DoltLab v2.0.0 to generate a SAML signing key and certificate. This script will create two files, ./saml_key.pem and ./saml_cert.pem DoltLab will use for signing SAML requests.
Finally, edit the ./docker-compose.yaml file for DoltLab so that the following arguments are added to the doltlabapi.command block and doltlabapi.volumes block:
doltlabapi:
command:
...
-samlKeyFile "/saml_key.pem"
-samlCertFile "/saml_cert.pem"
-samlMetadataDescriptor "/saml_metadata"
...
volumes:
...
- ${PWD}/saml_key.pem:/saml_key.pem
- ${PWD}/saml_cert.pem:/saml_cert.pem
- ${PWD}/saml_metadata:/saml_metadata # ./saml_metadata is the metadata descriptor downloaded from the IP
...Save these changes to the ./docker-compose.yaml file and restart your DoltLab instance for them to take effect.
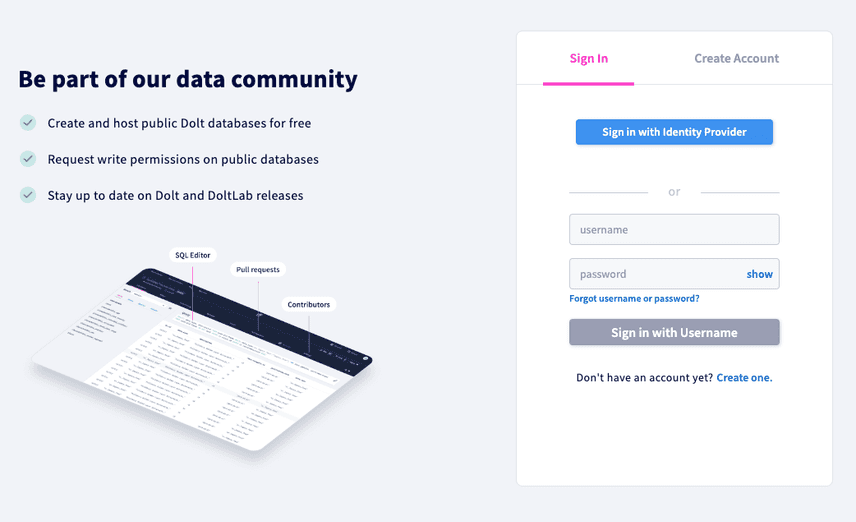
When SAML single-sign-on is configured for DoltLab, you will see the SAML option on the sign-in page:
Next, as user admin, login to your DoltLab instance and navigate to Profile > Settings > SSO.
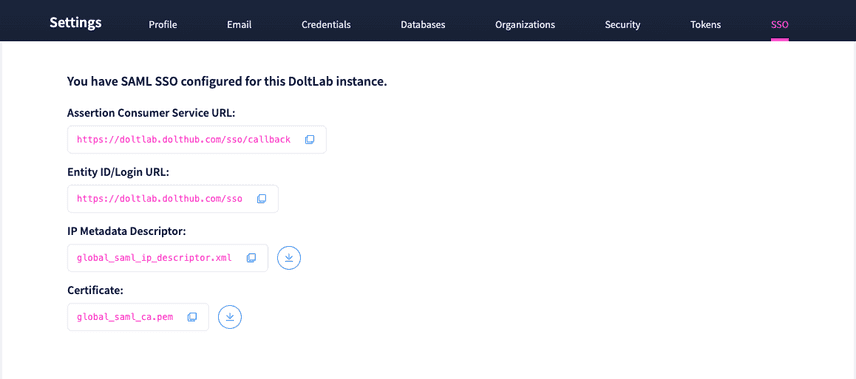
On this tab you will see the following:
Assertion Consumer Service Url displays the url where Okta should send the SAML assertion.
Entity ID/Login Url displays the url users can use to login to DoltLab using the IP, but they can now simply use the option available on the sign-in page.
IP Metadata Descriptor is a metadata descriptor for this DoltLab instance, and can be downloaded and supplied to the IP if it requires service providers to upload metadata.
Certificate can be downloaded if you want to add a signature certificate to the IP to verify the digital signatures.
Your DoltLab instance will now use single-sign-on through your IP for user login and account creation.
Conclusion
Stay tuned for more exciting updates coming soon for DoltLab Enterprise. Here's what you can look forward to in the coming months:
- Automated Backups—DoltLab will back up its data periodically and automatically to a location of your choice.
- Cloud Persistance—DoltLab will support the use of cloud resources for DoltLab services instead of local disk.
- Multi-Host Support—Deploy DoltLab's services across multiple hosts, for high availability/scalability.
- And more!
You can check out each of our different product offerings below, to find which ones are right for you:
- Dolt—it's Git for data.
- DoltHub—it's GitHub for Dolt.
- DoltLab—it's GitLab for data.
- Hosted Dolt—it's RDS for Dolt databases.